IDECSI,
a multi-application
audit solution
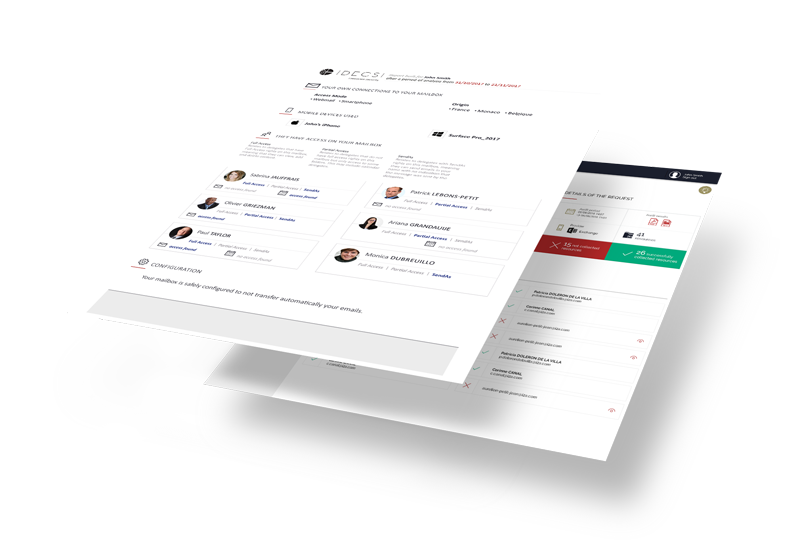
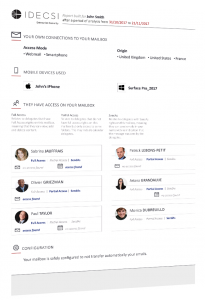
Are all accesses to your HR Team legitimate? Your executives? Your finance department?
Is your email configuration sound and up-to-date?
Can you guarantee the integrity of your OneDrive folders and your confidential SharePoint lists?
IDECSI allows you to perform a security audit on all of your key applications, whatever your environment.
A unique, one-click,
plug and play auditing platform
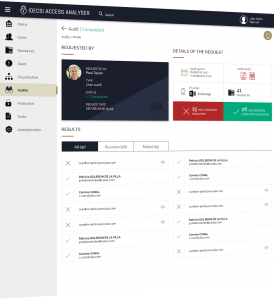
Identifies unauthorized internal and external access, privileged account abuse and malicious configuration.

See immediately
what’s at risk.

Reveal and prevent
malicious configuration
or unauthorized access.

Easily and regularly check
the integrity of your critical
applications and
your users' accounts.

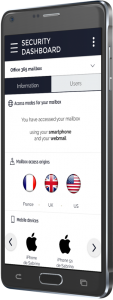
Give users visibility to
the security of their data
and engage them in
protecting the company.
IDECSI, a complete audit solution with
multiple options

Flash
Audit
IDECSI offers an immediate call-out service.
You decide the parameters : executives, specific users or even your entire company.
The IDECSI solution is plug-and-play.
After 14 days we present a detailed audit report with recommendations for resolving identified security issues.

On-demand
Audit
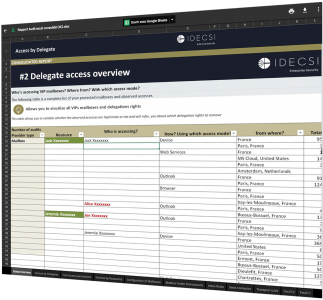
With IDECSI's On-demand Audit platform, you can check the integrity of any account or series of accounts in your company, at any time and with one click.
You decide the duration of the analysis from between 7 to 21 days.
Your Audit report is then edited automatically.

Permanent
Audit
IDECSI's Permanent Audit platform continuously monitors the accounts and applications you choose (all or just part of your company).
You can download the report immediately to see all access and configuration changes that occurred in the previous 30 days.
Principal applications which can be audited
Benefits of IDECSI’s
auditing solutions

Visibility
Nothing escapes you.
You benefit from a tool that gives crystal clear visibility on the security of your protected applications at any time.

Flexibility
You decide what you need and the solution is configured to fit: who should be covered, which applications to review, the frequency and duration of the analysis.

One click
Our auditing platform is smart and quick.
One click starts an analysis.

Positive user involvement
With IDECSI you enable your employees to participate in the security of the company. They see the audit results and can use these to check the access to and configuration of their applications.
Quick installation that
adapts to your environment
Make your applications 100% safe and protect users in one click, at any time, over any period and regardless of architecture.
Plug & Play
Installation in 2 hours

No compromise of existing data
No impact on users and on performance of your applications

Hybrid
On-premise
Cloud
Hybrid