IDECSI is a multi-application
intelligent solution for real-time
monitoring and audit
Is your email system compromised right now?
Is someone spying on your executives' emails?
Who’s browsing your sensitive SharePoint libraries?
IDECSI protects your critical applications On-premise, in the Cloud or Hybrid, and adapts to your business as it grows.
IDECSI is active and effective
in 3 simple steps

Intelligent
Diagnosis
Immediately see what’s at risk. Reveal and prevent existing malicious activity.
MAKE YOUR ENVIRONMENT 100% HEALTHY
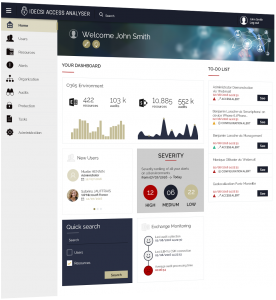
IDECSI performs an instant audit as soon as it is installed and confirms the status of each account - what are the current permissions, who can gain access and how, what devices are synchronized and which rules are set?

Personalized Protection
Benefit from personalized security monitoring for each user, based on their profile.
ACTIVATE INTELLIGENT PROTECTION
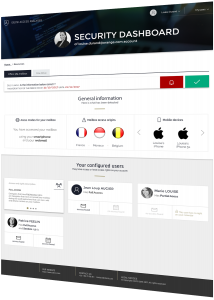
The initial diagnostic phase is based on IDECSI’s machine-learning technology. Protection is personalized, based on the individual user profiles. IDECSI's technology distinguishes legitimate actions so that only dangerous actions are reported.

24x7 Real-time detection
Identify an intrusion or threat the instant it occurs.
BE ALERTED IN REAL-TIME
No unauthorized access or configuration can escape you. Alerts can be sent to users for optimal awareness and minimal processing times. They can also be sent to the security or IT team, SIEM or SOC.
Principal applications protected by IDECSI
IDECSI can also protect your proprietary and industry specific applications: contact us!
Benefit from the engagement of all employees in the protection of your company
Everyone considers their own safety and that of the company. IDECSI creates a privileged channel of communication and information between the security team and users.
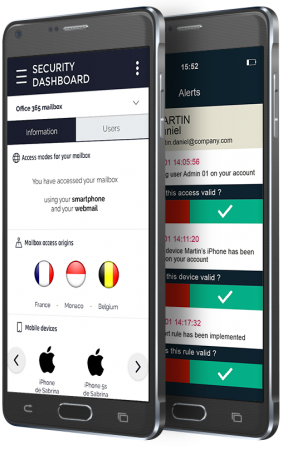
Thanks to IDECSI’s smartphone app, each employee can naturally participate in the protection of their data.
Employees are alerted in case of breach, unauthorized access or malicious settings in their accounts. With a single click, they can then report the incident through their smartphone to the security teams.
IDECSI provides a communication channel dedicated to security.
The benefits of increased
participation in security
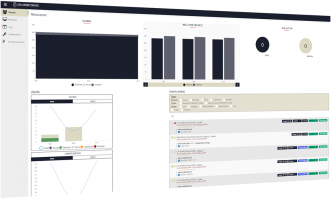
IDECSI improves the effectiveness of your SIEM, while reducing the costs. By pre-processing the huge volume of application logs, IDECSI identifies the real anomalies without massively increasing SIEM investment, providing your security team with more accurate, real-time, actionable data.

User-centric
Users are engaged in the security of the company and participate in collective defense, which is now essential.

ROI
Processing and analysis costs are very low. Security teams and SOC can focus only on the real security events. All normal events are processed by IDECSI and filtered out. Breaches are confirmed by users.
Time saving
Resolution time is extremely short. The breah alert is processed by the person who's directly concerned.

Flexibility
You can decide and easily change the applications and the users being protected. One-off or continuous audit and monitoring functions with or without alerting.

Efficiency
The ability to detect breaches is significantly enhanced.
All users are engaged and can contribute by immediately highlighting the threats to their accounts.
No false positives
Our intelligent detection technology focuses on useful alerts. Users will experience only 0.3 to 1.7 * alerts per year.
* On average, depending on user profiles.
Quick installation that
adapts to your structure
and environment
Make your applications 100% safe and protect their users in one click, at any time, over any period of time and regardless of the technical architecture.
Plug & Play
Installation in 2 hours
Automatic configuration
Learning mode

No compromise of existing data
No impact on users and on performance of information system

Hybrid
On-premise
Cloud
Hybrid