IDECSI delivers cutting edge technology
and engages all employees in effective,
cost-efficient cyber security
Continuous real-time analysis of data – access logs, admin logs, configuration objects – machine learning, behavioral analysis, individualized protection, context management and real-time alerting, SIEM and SIRP integration.

Intelligent, application aware security

Personalized protection

3 levels of continuous analysis
Intelligent, application aware security.
Continuous update of the risks.
A complete risk repository for each protected application
What are the possible attack vectors against your email platform? Against your collaboration tools or against your proprietary applications? What potentially dangerous actions can be taken by someone with your password , or by your IT administrator, or by someone with their credentials?
With the IDECSI platform, you can detect unauthorized access or malicious operations without being an expert in the secured applications, and without a long and expensive configuration project. IDECSI is natively preconfigured with a risk repository specific to each protected application. Each operation performed is verified. If the operation is potentially dangerous, it immediately triggers our real-time analysis processing. Therefore, the IDECSI platform is immediately operational.
Continuous risk updates
The IDECSI risk repositories are constantly updated to provide up-to-date security throughout the life of the protected application.
Personalized protection, unique for
each user – no false positives
Continuous log processing and real-time analysis
For each application and for each protected user the IDECSI platform collects the relevant information – access logs, administration logs, configuration objects. This data is analyzed in real time by our big data platform using our optimized algorithms.
Machine learning
Behavior analysis for individualized protection
For each protected user and resource, the IDECSI platform combines machine learning and behavior analysis to generate individual protection profiles. Each person benefits from personalized protection based on their mode of operation.
In addition, the IDECSI platform provides a summary of the user’s configuration in easy‑to‑understand, non-technical language. This can be validated by the individuals concerned.
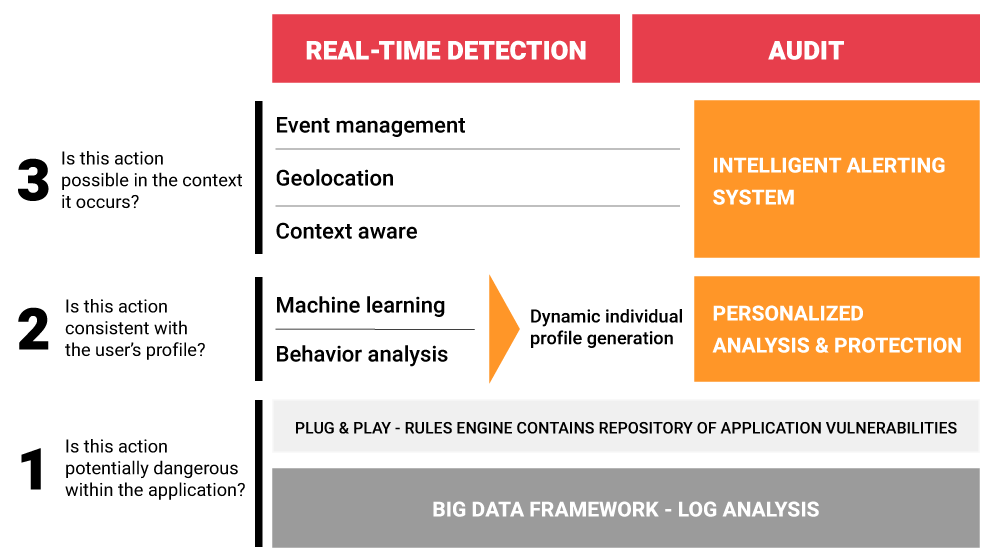
3 stages of continuous risk analysis
with real-time alerting
1
Is the operation described in the logs potentially dangerous?
The IDECSI platform continuously collects millions of logs and objects generated by the protected applications.
Each action is analyzed against the application’s risk repository to determine if it is potentially dangerous. If so, the second stage of analysis is activated.
2
Is the operation compatible with the individual profile?
The IDECSI platform checks whether the operation performed is legitimate. Does it match the profile of the protected person or resource? Are the user, the access mode, the origin of the access, and the behavior displayed consistent ? If any of the criteria do not match, an alert is immediately generated. If all criteria are consistent, the IDECSI platform activates the third stage of analysis.
3
Is the context of the action valid?
The IDECSI platform verifies that each operation is possible in the context in which it occurs. For example, if your email is accessed from London at 10:45 and SharePoint from New York at 10:52, the platform will alert.
This third stage of intelligent analysis is essential and is one of the ways in which IDECSI identifies password theft.
Your users and applications are protected
regardless of your application architecture:
On-premise, Cloud or Hybrid
Hybrid architecture allowing native integration
with SIEM or SIRP
The IDECSI platform can enhance and optimize your central analysis tools, whether SIEM or SIRP.
Information managed by IDECSI, including alerts and notifications, can be sent to the SIEM or SIRP in native format, taking advantage of the integration mechanisms they provide.
Since the SIEM and SIRP are by nature protected and are typically not accessible from outside the network, the IDECSI connector deployed within your environment can receive data from the IDECSI cloud platform, transform it into native format and send to the SIEM or SIRP using the interfaces provided.